Política de seguridad para usuarios en Atlassian: puntos a tener en cuenta
En determinadas situaciones, tenemos la necesidad de establecer políticas de seguridad para nuestros usuarios, entre ellas, el reseteo de contraseñas cada cierto tiempo, por ejemplo. Esta política y otras reglas de autenticación podemos configurarlas en nuestras instancias de Atlassian Cloud.
A continuación, compartimos una recopilación de los puntos más importantes a tener en cuenta:
1. Verificación de Dominio
El primer requisito imprescindible para poder trabajar con las políticas de seguridad y autenticación es verificar el dominio. Sin esta verificación no es posible asignar ninguna política de autenticación.
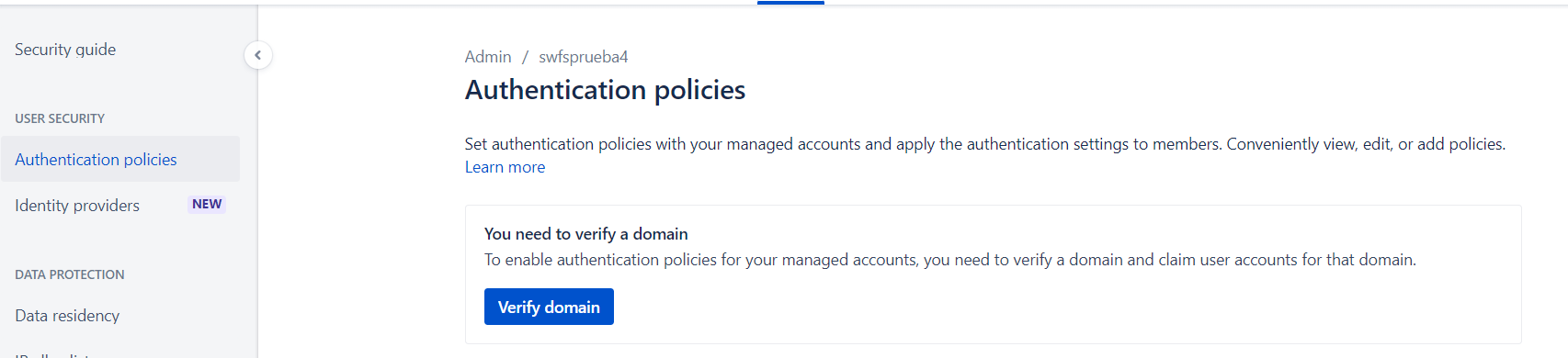
Ayúdate de este artículo si necesitas localizar los pasos a seguir: Understand authentication policies | Atlassian Support
Esta verificación de dominio se puede realizar en cualquier instancia, tanto si ya se ha instalado la extensión Atlassian Access como si no se ha hecho. La diferencia principal es que, si no tenemos Atlassian Access, solo podemos establecer una única política de autenticación para todos los usuarios. Sin embargo, si tenemos Atlassian Access podremos establecer varias políticas de autenticación por cada grupo de usuarios que tengamos sincronizado. Tendremos más flexibilidad a la hora de configurar los requisitos de contraseña segura para cada grupo de usuarios.
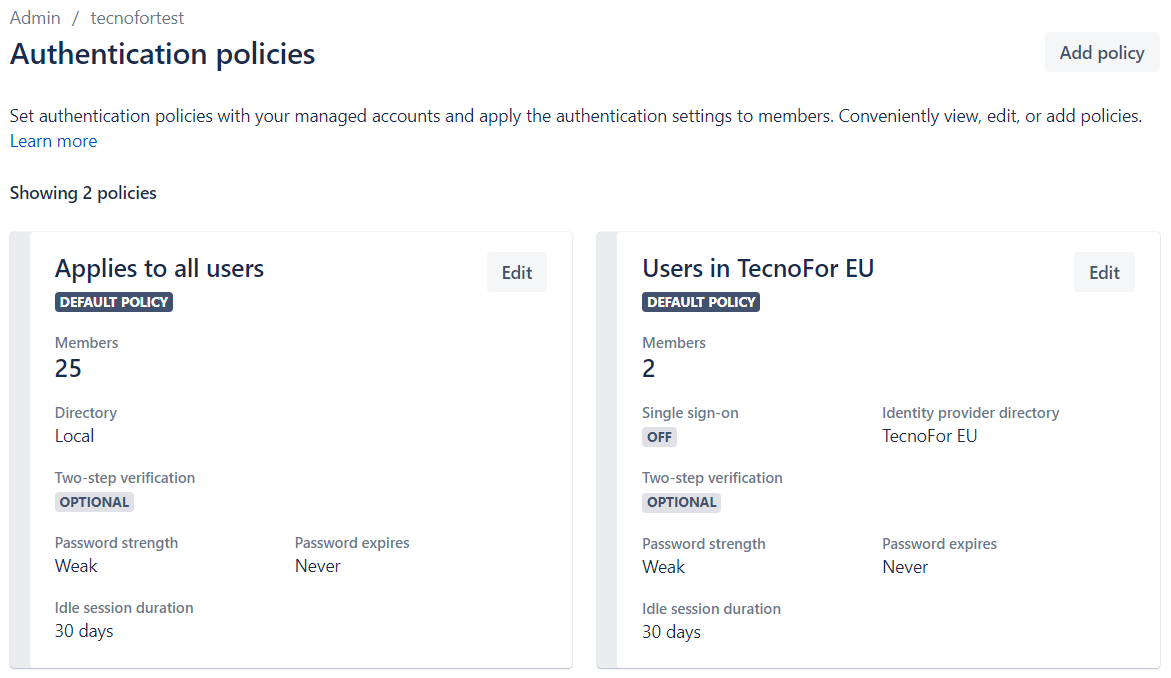
2. Creación de políticas
Una vez realizada la verificación de dominio o dominios, ya podremos añadir nuestra política de autenticación.
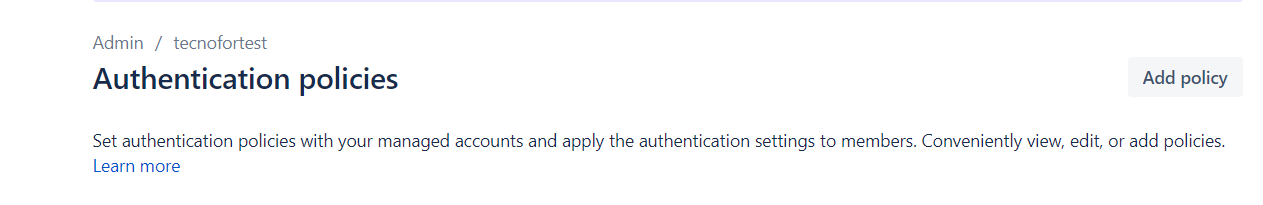
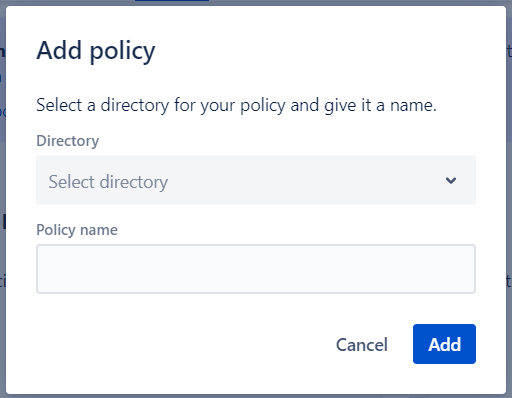
A la hora de la creación tendremos que decidir un nombre para la política. En el caso de que tengamos Atlassian Access podremos seleccionar el directorio de entre todos los que tengamos vinculados.
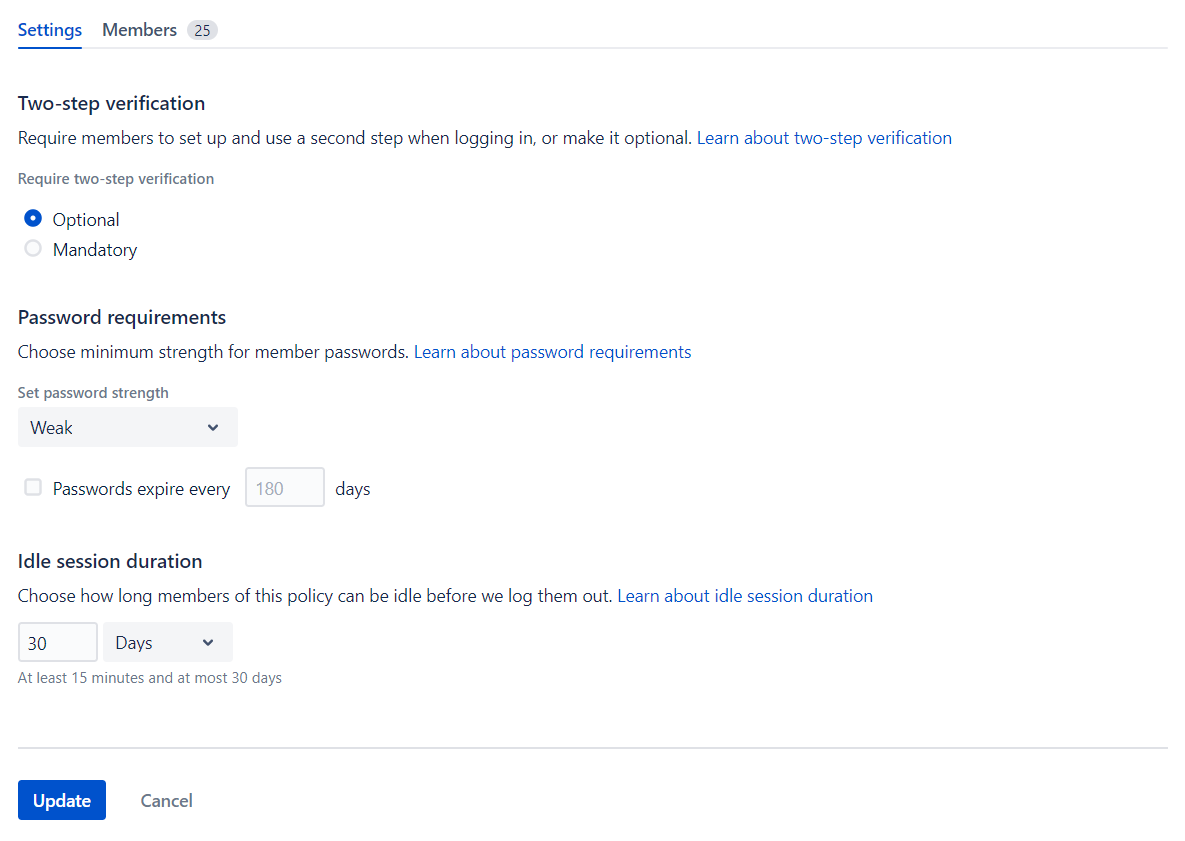
Una vez creada la política, podremos definir los siguientes ajustes:
- Verificación en dos pasos.
- Establecer el nivel de seguridad de la contraseña y la expiración.
- Duración de la sesión.
3. Establecer caducidad de contraseña
Si has llegado hasta aquí y no tienes claros los pasos exactos que hay que dar para establecer la caducidad de las contraseñas, el resumen sería el siguiente:
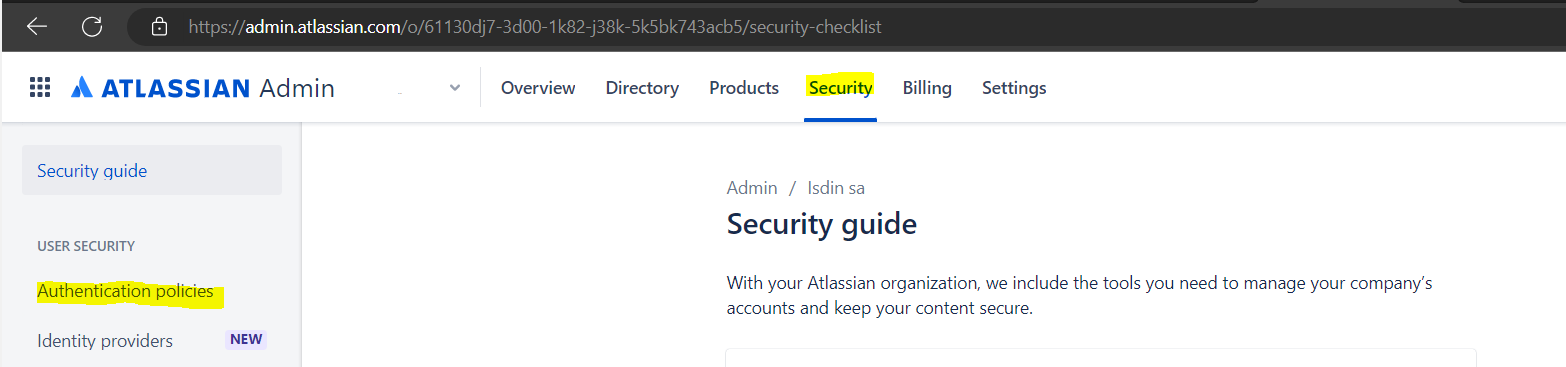
- Vamos a atlassian.com. Seleccionamos nuestra organización.
- Seleccionamos Seguridad> Políticas de autenticación.
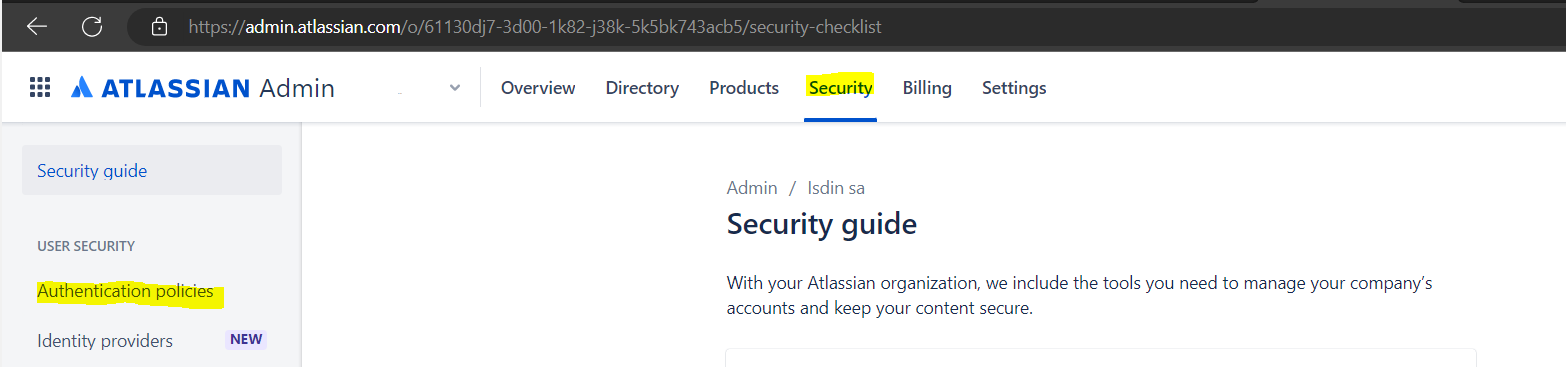
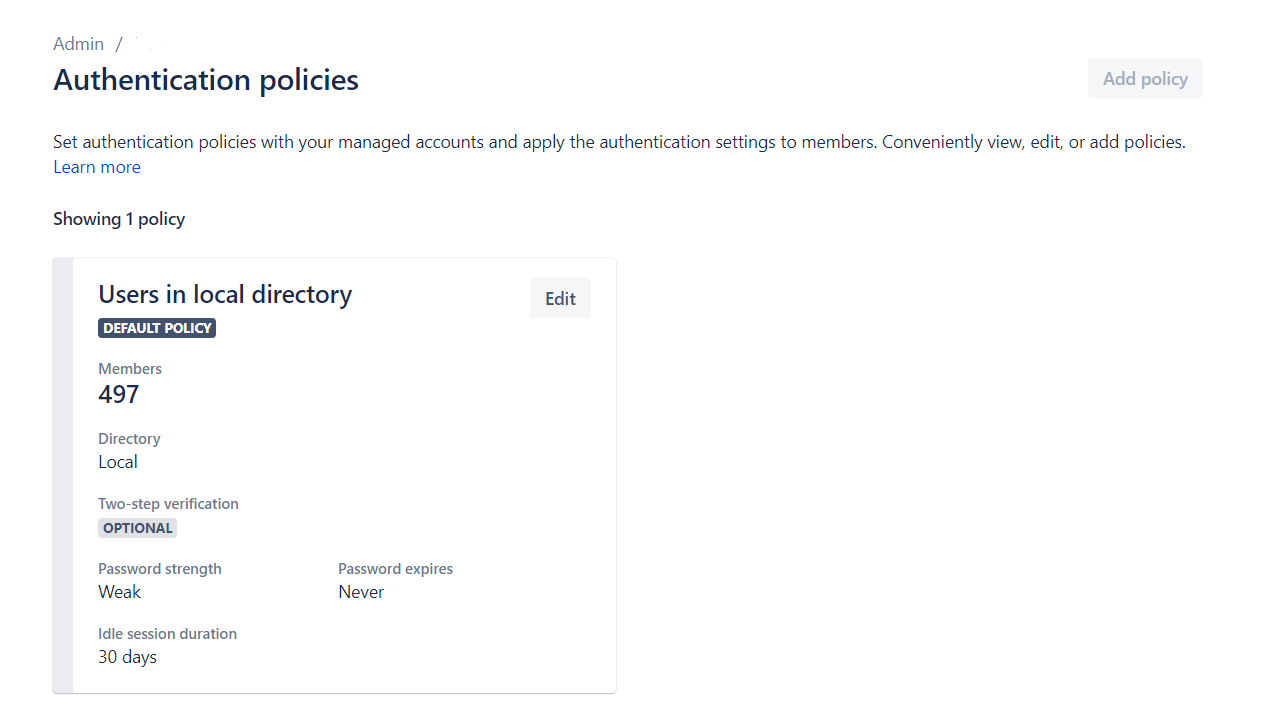
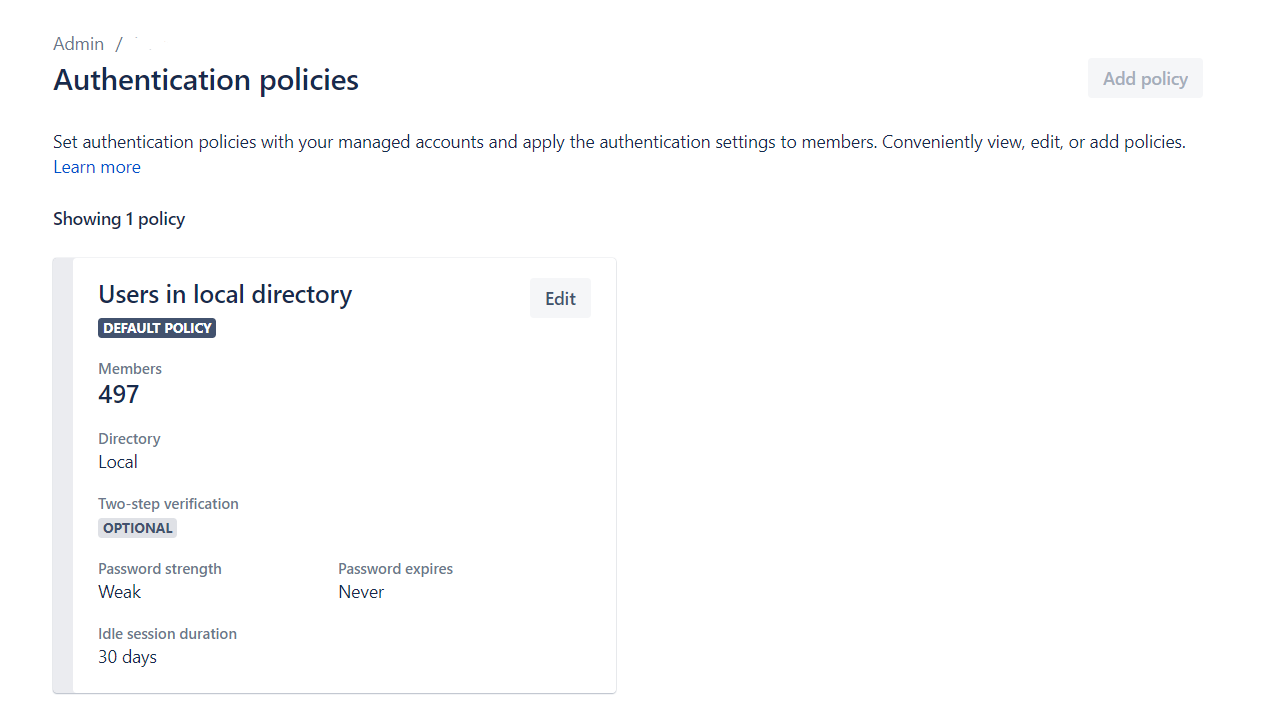
3. Seleccionamos Editar para la política que queremos modificar.
4. En la página Configuración, seleccionamos Seguridad y caducidad de la contraseña.
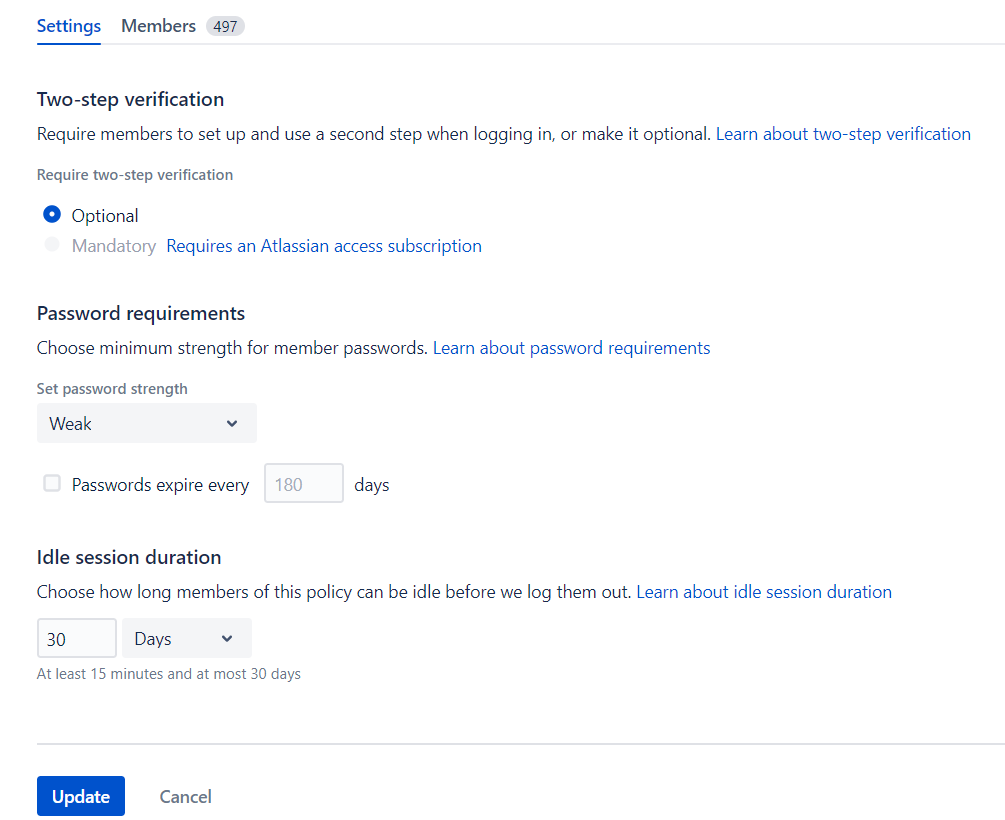
5. Una vez establecido el período (en días) en el que queremos que las contraseñas caduquen, seleccionamos actualizar.
6. Para aplicar la configuración de contraseña a los miembros de inmediato, podemos seleccionar restablecer contraseñas.
La próxima vez que un usuario inicie sesión, le pediremos que cree una nueva contraseña.
4. Restablecer contraseñas
Si lo que nos interesa es restablecer las contraseñas de todos los usuarios de forma manual y asegurarnos que cuando inicien sesión la cambien, entonces podemos saltarnos varios pasos e ir directamente a este punto. Si vas a realizar este reseteo masivo, recomendamos informar a los usuarios. Ya que el cierre de sesión puede tardar unos minutos y se puede perder parte del contenido cuando restablezcan su contraseña de nuevo (por ejemplo, si estabas realizando alguna acción que no han guardado).
- Vamos a atlassian.com. Seleccionamos nuestra organización.
- Seleccionamos Seguridad> Políticas de autenticación.
3. Seleccionamos Editar para la política que queremos modificar.
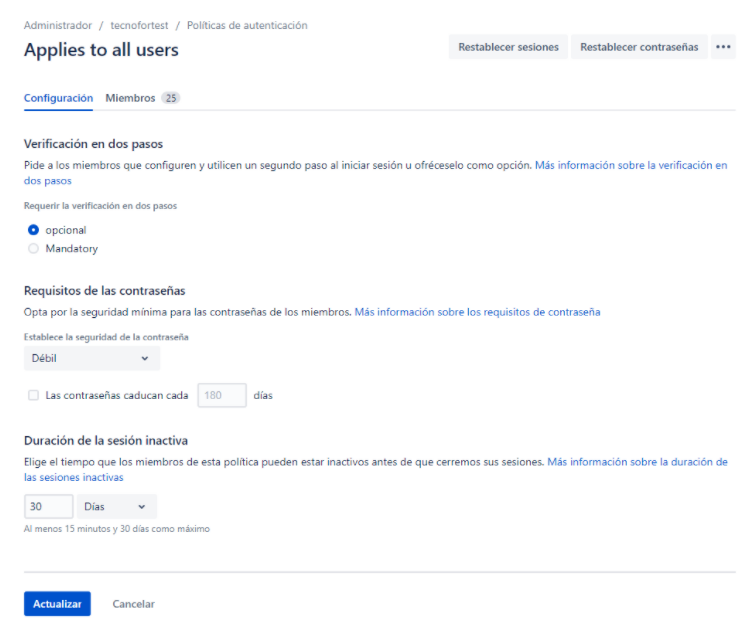
4. Seleccionamos Restablecer contraseñas.
5. La próxima vez que un usuario inicie sesión, le pediremos que cree una nueva contraseña.
5. Establecer una política de autenticación
Cualquier política de autenticación que se configure, aplicará a cualquier producto de Atlassian Cloud:
- Bitbucket.
- Confluence.
- Jira Work Management.
- Jira Software.
- Jira Service Management (solo para usuarios de cuentas de Atlassian con dominios verificados). No se pueden crear políticas de autenticación para los usuarios customer de un portal de Jira Service Management.
- Estas cuentas de clientes tendrán solo un requisito a nivel contraseña: a la hora de crearla, tendrán que tener entre 8 y 100 caracteres de longitud. Puedes obtener más información sobre las cuentas solo del portal.
Ten en cuenta también que:
- Podemos pedir a los usuarios que usen la verificación de dos pasos al iniciar sesión o por el contrario mantenerlo como opción:

- Podemos establecer el tiempo que mantenemos la sesión de usuario con vida, por seguridad podemos hacer que un usuario se tenga que loguear como mínimo cada 15 minutos y como máximo 30 días.
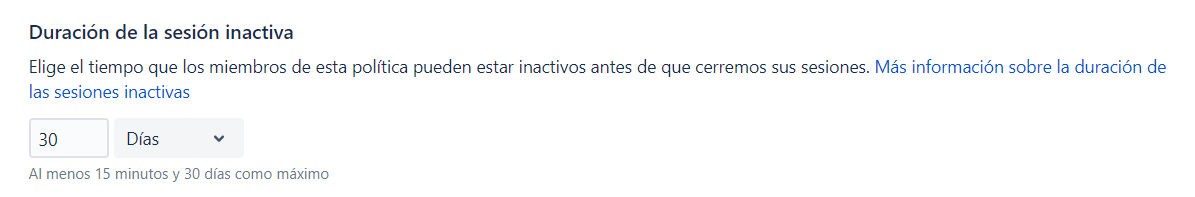
En futuros artículos trataremos sobre estos dos temas en profundidad.
Mientras tanto, esperamos que esta información haya sido de tu utilidad.
Sam García 17 de enero de 2023